what’s trending
Editor's Pick
Latest Articles
Setting up a home network often leads to a moment of hesitation. You check your available connections and see two nearly identical names from the same router. One usually ends in [...]
Choosing between a laptop and a tablet was once a simple exercise in compromise. You purchased a laptop for serious work and reserved the tablet for casual reading or movies. Today, [...]
You unbox a shiny new laptop or smartphone expecting a clean slate. Instead, you are greeted by a cluttered screen filled with unwanted games, trial antivirus programs, and obscure shopping apps. [...]
That sudden splash is the sound of a modern nightmare. Your phone just hit the water, and your instinct is to freeze in disbelief. Don't freeze. Immediate action is the only [...]
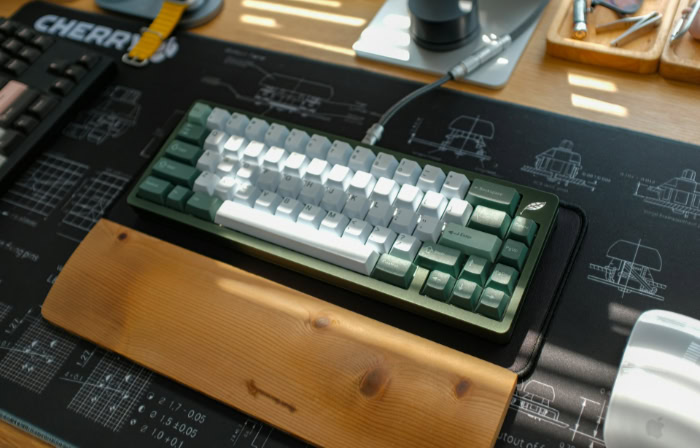
Every PC setup eventually hits the same fork in the road: the choice between established tradition and bleeding-edge speed. For decades, mechanical switches reigned supreme as the gold standard for enthusiasts. [...]
Cryptocurrency is a form of digital or virtual currency that uses cryptography for security. Unlike traditional fiat money like the US Dollar or Euro, it operates without a central authority. No [...]