What Is Tor Browser? Breaking Barriers to Online Freedom
Privacy online is becoming harder to achieve, yet for those seeking to browse the internet anonymously or bypass censorship, Tor Browser offers a powerful solution. Designed with privacy in mind, Tor protects users by encrypting their internet traffic and routing it through a global network of servers, making it nearly impossible to trace their online activity.
This unique functionality has made it indispensable for individuals facing surveillance, restrictive governments, or those working to safeguard sensitive information.
Definition and Core Functionality
The Tor Browser is built on the principles of anonymity and security, leveraging advanced technologies to obscure a user’s online identity and location. Central to its operation is the Tor network, a system designed to protect privacy through complex traffic routing and encryption techniques.
To fully appreciate how Tor Browser achieves its goals, it’s important to understand how the underlying network functions and the specific mechanisms that make it unique.
What Is the Tor Network?
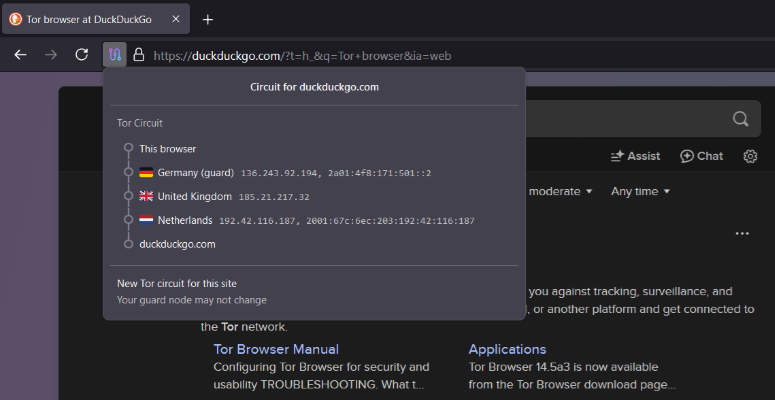
The Tor network (short for “The Onion Router”) is a decentralized system designed to provide anonymity for internet users. Its name comes from the concept of onion routing, a method that encrypts and layers data multiple times before sending it through a series of computers, referred to as nodes or relays.
Each layer of encryption is peeled away by a different node before forwarding the traffic to the next step in the system, much like peeling layers off an onion.
This process prevents any single entity from seeing the full picture of what a user is doing online. For example, the initial node knows the user’s IP address but not the destination of their traffic, while the final node (known as the exit node) knows the traffic’s destination but not the user’s origin.
The intermediate nodes only see their immediate predecessor and successor, ensuring no single point in the network has access to both the source and destination of the data. This layered encryption provides a robust framework for protecting user privacy and resisting surveillance.
How Tor Browser Works
Tor Browser operates as a specialized web browser that connects users to the Tor network, routing their internet traffic through multiple nodes to mask their identity. When a user initiates a connection, their traffic is randomly directed through at least three relays: the entry node, middle node, and exit node.
The entry node establishes the first connection between the user and the Tor network, encrypting their traffic and hiding their IP address. Next, the middle node acts as an intermediary, adding another layer of separation between the user and their eventual destination.
Finally, the exit node decrypts the last layer of encryption and sends the traffic to its final destination, such as a website. Because the exit node only sees encrypted traffic data and not the user’s IP address, anonymity is preserved throughout the process.
This system relies on volunteer-operated relays, individuals and organizations that provide the infrastructure for the Tor network. By contributing bandwidth to the network, these volunteers help ensure the system remains decentralized and effective.
Unlike conventional browsers, which directly connect users to websites, Tor Browser prioritizes privacy, often at the expense of speed due to the multiple routing steps involved.
Onion Services (.onion Sites)
Beyond browsing regular websites anonymously, Tor also enables access to onion services, which are special websites hosted within the Tor network that use the .onion domain. These sites, often referred to as the dark web, are inaccessible through standard browsers and conventional internet connections.
Onion services are designed to offer privacy to both users and website operators. Unlike traditional websites, they do not expose their server’s IP address, further enhancing security.
This is particularly valuable for those hosting whistleblowing platforms, secure communication tools, or other resources that require protection from surveillance or censorship.
Accessing .onion sites requires Tor Browser, which automatically recognizes and connects to these domains using the same principles of anonymity and encryption as regular browsing. While onion services have a reputation for hosting illicit content, they also serve as a vital resource for individuals and organizations operating in restrictive environments, offering a way to share information and communicate securely without fear of interception.
Key Benefits and Use Cases
Tor Browser has gained a reputation as one of the most effective tools for safeguarding online privacy and countering digital restrictions. Its unique capabilities make it a valuable resource for a wide range of users, from individuals seeking personal anonymity to professionals operating under challenging conditions.
Anonymity and Privacy
Personal privacy is one of the most significant advantages offered by Tor Browser. It shields users from being tracked by masking their IP addresses, which serve as digital identifiers.
Websites, advertisers, and even internet service providers (ISPs) are unable to pinpoint a user’s physical location or link their browsing activity to a specific device, thanks to the Tor network’s traffic-routing methods.
In addition to hiding IP addresses, Tor prevents the creation of detailed browsing profiles. Advertisers and trackers commonly use cookies and metadata to build profiles of users’ habits and interests, but Tor’s ability to isolate browsing sessions ensures these efforts are largely ineffective.
The browser also clears cookies and browsing history automatically after each session, offering an added layer of protection.
Tor is particularly effective for individuals concerned about surveillance or data breaches. By encrypting traffic and obfuscating its origin, it makes unauthorized monitoring of browsing activity far more difficult.
For those who value online privacy or face potential risks from being tracked, such measures are indispensable.
Circumventing Censorship
Government-imposed firewalls and ISP restrictions can significantly limit access to the open internet, especially in regions with heavy censorship. Tor Browser provides a critical solution for bypassing these barriers by disguising the source and destination of a user’s internet traffic.
Through its multi-node routing, it becomes nearly impossible for censors to determine what sites or services are being accessed.
Obfuscated bridges, a feature offered by the Tor network, add another layer of functionality for users facing aggressive state censorship. These bridges are specialized entry points into the network that prevent traffic from being identified as originating from Tor.
This prevents governments and ISPs from blocking access to the network itself, allowing users to reach content that would otherwise be restricted.
Internet freedom is particularly valuable for individuals living in repressive environments. Whether accessing unbiased news sources, educational materials, or social media platforms, tools like Tor provide individuals with the means to communicate and stay informed without fear of their activity being traced or restricted.
Critical Use Cases
The ability to maintain anonymity and bypass censorship makes Tor Browser an indispensable tool for certain groups who face heightened risks online. Journalists, for instance, rely on Tor to communicate securely with colleagues and sources while protecting the confidentiality of their investigations.
In an era where authorities and adversaries monitor digital communications extensively, such safeguards are essential for the integrity of independent reporting.
Activists and human rights defenders also use Tor to organize and share information in regions where their work could lead to harassment or reprisal. By hiding their internet activities, they reduce the risk of being identified and targeted by hostile groups or governments.
Tor has become a lifeline for individuals fighting for democracy, freedom of speech, and social justice.
Whistleblowers, who often expose corruption or wrongdoing, face similar risks and rely heavily on Tor to share sensitive information without risking their safety. Organizations that receive whistleblower submissions, such as news outlets and advocacy groups, also use Tor to maintain secure channels of communication and safeguard their sources.
In addition to professionals, everyday users in heavily censored regions turn to Tor to access blocked resources and communicate freely with the outside world. Simple actions like reading news or connecting with family abroad can become impossible under strict government surveillance, but Tor offers a practical workaround.
Whether for professional or personal purposes, the browser continues to serve as a critical tool for those requiring online anonymity and freedom.
Limitations and Security Considerations
Tor Browser relies on a sophisticated system to protect user privacy, but its design comes with certain inherent challenges and risks. From performance slowdowns to security vulnerabilities and legal obstacles, users must be aware of these factors to use the browser effectively and safely.
Performance Trade-offs
One of the most noticeable limitations of Tor Browser is its slower browsing speed compared to traditional browsers. This slowdown is a result of the multi-node routing system that reroutes internet traffic through several relays around the world.
Each step in the process introduces additional latency, which can lead to delays when loading websites or accessing online services. The encryption applied at each node also adds to the overall processing time.
The decentralized nature of Tor means it cannot match the speed or efficiency of centralized networks like VPNs or standard browsing routes. For users accustomed to fast internet connections, the difference in speed can be frustrating, particularly when streaming video, downloading large files, or engaging in other bandwidth-intensive activities.
Tor’s emphasis on privacy over performance is a necessary trade-off, but potential users should be aware of the slower experience.
Security Risks
While Tor offers robust privacy protections, it is not immune to security risks. Exit nodes, the final points in the routing chain, can pose a significant vulnerability.
Traffic leaving an exit node is decrypted before it reaches its final destination, which means that anyone operating a malicious exit node could potentially monitor unencrypted data, such as login credentials or personal information sent over HTTP connections. Users are strongly advised to prioritize HTTPS websites, which encrypt traffic at the application level, to mitigate this risk.
Malicious relays can also be deliberately introduced into the Tor network by adversaries seeking to intercept or analyze traffic. While the network attempts to detect and block these nodes, the decentralized, volunteer-run structure makes it difficult to eliminate them entirely.
Another potential vulnerability lies in deanonymization attacks, where advanced techniques are used to correlate internet traffic and identify users despite their use of Tor. Government agencies and hackers with significant resources have occasionally targeted Tor users in this way.
Even though these risks are well-documented, they mainly affect specific threat models, such as individuals targeted by highly motivated adversaries. For most users, Tor provides a level of privacy that greatly exceeds what is available through conventional browsers.
Legal and Practical Challenges
In some regions, access to Tor Browser itself is restricted. Governments that view anonymity tools as a threat often block access to the network by monitoring and filtering internet traffic.
In extreme cases, using Tor may even be illegal, exposing users to potential legal consequences. Individuals in such jurisdictions must exercise caution and consider additional safeguards, like obfuscated bridges, when attempting to access the Tor network.
Workplace or ISP policies can also present barriers. Some employers and internet providers actively monitor for Tor traffic and may flag or block its usage, even in contexts where it is legal.
The distinctive patterns of encrypted traffic generated by Tor can make it easier to detect, especially when no additional steps are taken to disguise it.
Practicality is another concern, as some websites actively restrict access from known Tor exit nodes. This is often done to prevent abuse, such as spam or malicious activity, which may originate from users taking advantage of Tor’s anonymity.
As a result, users may encounter difficulty accessing certain services or find themselves required to complete additional verification steps, further complicating their browsing experience.
Comparison with Privacy Alternatives
Tor Browser is not the only tool available for those seeking to protect their privacy online, but it offers a distinct approach compared to alternatives such as virtual private networks (VPNs) and private browsing modes. Each of these tools has its own strengths and weaknesses, making certain options more suitable depending on an individual’s specific needs.
Tor vs. VPNs
Both Tor and VPNs aim to enhance online privacy, but they achieve this through fundamentally different methods. Tor relies on a decentralized network composed of volunteer-operated nodes to anonymize a user's activity.
Traffic is routed through multiple nodes, with each layer of encryption stripped away by a different node, making it difficult to trace both the origin and destination of the traffic. This decentralized architecture ensures no single entity can control or monitor user activity across the network, providing robust anonymity.
VPNs, on the other hand, use a centralized model. A VPN service provider operates the servers to which users connect, creating an encrypted “tunnel” between the user and the internet.
All traffic appears to originate from the VPN server rather than the user's actual IP address, which prevents ISPs and third parties from monitoring browsing activity. However, since all data passes through the VPN provider, trust in the service is essential.
A poorly managed or malicious VPN could potentially log user data or share it with third parties.
Tor is better suited for individuals requiring strong anonymity, such as journalists or activists working in high-risk environments. VPNs, while offering less anonymity, are often faster and more user-friendly, making them a good choice for everyday usage, such as accessing geo-restricted content or securing public Wi-Fi connections.
Tor vs. Private Browsing Modes
Private browsing modes, such as those offered by Chrome or Firefox, are often misunderstood as tools for privacy. They prevent local data, including browsing history, cookies, and login credentials, from being stored on a user's device.
However, private browsing does not hide the user's IP address or encrypt internet traffic. Websites, ISPs, and other third parties can still track activity during a private browsing session unless additional measures, like a VPN or Tor, are employed.
Tor, in contrast, provides anonymity by masking the user's IP address and routing traffic through multiple relays. While private browsing keeps a user’s activity hidden from others using the same device, Tor hides activity from external entities such as trackers, oppressive regimes, or online advertisers.
For users who only want their browsing sessions to remain private locally, private browsing modes are often sufficient. Tor is the better option for those who need protection against external surveillance or censorship.
When to Use Tor (and When Not To)
Tor is ideal for situations where anonymity and censorship resistance are critical. Individuals living in regions with heavy internet restrictions rely on Tor to access blocked websites, communicate securely, and share information freely.
Activists, whistleblowers, and journalists often turn to Tor to protect their privacy when working on sensitive or high-risk matters.
However, Tor may not always be the best choice for day-to-day browsing. Its slower speed can be a drawback for streaming, gaming, or other data-intensive activities.
Additionally, some websites block Tor users due to concerns about potential abuse. For casual browsing, shopping, or accessing region-locked content, a VPN offers greater convenience and faster speeds.
Users concerned about privacy but with no specific need for anonymity on the scale provided by Tor may also find private browsing modes coupled with a VPN a better solution for their everyday needs. Choosing the right tool depends on the balance a person seeks between privacy, speed, and functionality.
Conclusion
Tor Browser plays a vital role in the realm of digital privacy, offering individuals a way to browse the web anonymously, bypass censorship, and protect sensitive information from prying eyes. Its innovative use of onion routing and decentralized infrastructure makes it one of the most powerful tools for safeguarding online identities and ensuring access to information, especially for those operating in regions with strict surveillance or oppressive controls.
By prioritizing privacy over convenience, Tor has established itself as a lifeline for journalists, activists, whistleblowers, and everyday users in need of greater online safety.
While Tor’s strengths are undeniable, its limitations highlight the importance of understanding the context in which it is best utilized. Slower speeds, security risks at exit nodes, and challenges posed by legal or workplace restrictions underscore the fact that no privacy tool is perfect.
Additionally, ethical considerations surrounding the misuse of Tor for illegal activities add a layer of complexity to its reputation.
Despite these challenges, Tor remains a critical resource in the fight for privacy and internet freedom. In a world where online surveillance and censorship are growing concerns, its ability to offer anonymity and protect digital rights makes it an indispensable tool for those seeking to reclaim control over their online presence.


