What Is a VPN? How It Protects Your Digital Freedom

Protecting your online presence has never been more important. As cyber threats grow and digital surveillance becomes a pressing concern, many people are searching for effective ways to keep their data safe, browse privately, and access restricted content.
This is where VPNs, or Virtual Private Networks, come into play. They serve as a powerful tool to enhance online privacy, secure your internet connection, and unlock content across the globe. But how exactly do they work, and are they truly worth it?
How VPNs Work: Core Functionality
Virtual Private Networks (VPNs) are designed to protect your online activities from prying eyes by implementing advanced technologies that secure your internet connection and conceal your digital footprint. They achieve this by combining encryption and IP masking, two essential processes that enhance privacy, security, and accessibility.
Each component plays a vital role in ensuring users can browse the internet with confidence while maintaining control over their data.
Encryption Basics
At the heart of VPN functionality is encryption, a process that transforms your data into unreadable code as it travels across the internet. By doing this, VPNs prevent unauthorized parties from intercepting or deciphering sensitive information, such as passwords, financial details, or personal messages.
Modern VPNs rely on advanced encryption protocols to achieve this level of security. For example, OpenVPN, one of the most widely used protocols, balances speed and encryption strength for secure connections.
WireGuard, another cutting-edge protocol, has gained attention for its simplicity, efficiency, and high performance, making it an appealing choice for many users.
Encryption ensures that any data sent between your device and the internet remains protected from hackers, internet service providers (ISPs), and even government surveillance. Even when connected to public Wi-Fi networks, which are notorious for being insecure, your VPN encrypts your information, turning a vulnerable connection into a secure one.
IP Masking
Another critical feature of VPNs is their ability to mask your IP address. An IP address functions like a digital identifier, revealing details about your location and the device you’re using.
When you connect to a VPN, your internet traffic is routed through a remote server operated by the VPN provider. This process replaces your original IP address with the IP address of the VPN server, effectively obscuring your location and making it difficult for anyone to trace your online activity back to you.
IP masking not only enhances privacy but also helps users bypass location-based restrictions. Many websites and online services, such as streaming platforms or social media sites, restrict access based on geographic location.
By connecting to a VPN server in a different region, you can appear as though you’re browsing from that location, granting access to content that may otherwise be unavailable. Similarly, masking your IP address can help protect against profiling by advertisers or prevent malicious actors from targeting you based on your location.
Security and Privacy Benefits
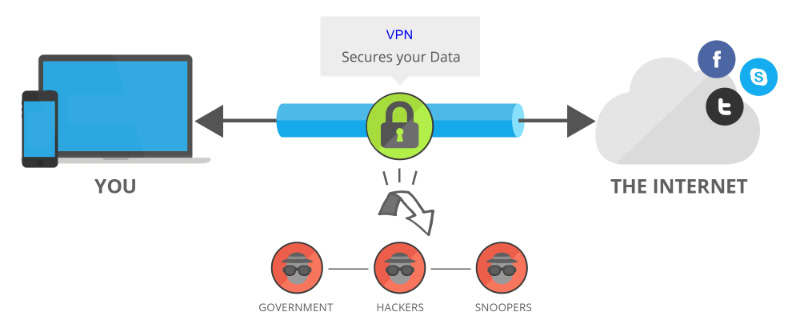
A VPN is more than just a tool for accessing restricted websites; it is a vital resource for protecting your sensitive information and maintaining control over your online identity. By combining advanced security measures with privacy-focused features, a VPN equips users with the tools they need to stay safe and maintain control over their online activities.
Data Protection
Protecting your personal data is one of the foremost advantages of using a VPN. In many cases, the internet connections we rely on daily, such as public Wi-Fi networks in coffee shops or airports, are highly vulnerable to cyberattacks.
Hackers can intercept these unsecured networks and gain access to sensitive information like passwords, financial details, and private messages. A VPN encrypts your internet connection, making it virtually impossible for unauthorized parties to decipher your data.
Additionally, VPNs shield users from potential surveillance by ISPs. Internet providers often track browsing habits, sell user data to advertisers, or throttle connection speeds based on usage.
By encrypting your connection, a VPN blocks these entities from monitoring or interfering with your activity, providing an added layer of security and peace of mind.
Anonymity
Maintaining anonymity online is increasingly important in a world where everything from websites to governments is working to track user behavior. A VPN achieves this by concealing your IP address and masking your location.
Instead of your real digital identifier being visible, websites and trackers see the IP address of the VPN server you’re connected to.
Advertisers use your browsing habits to target you with personalized ads, while malicious actors can leverage your data to create scams or phishing attempts. Governments and institutions in certain regions impose even stricter monitoring or censorship, making anonymity essential for accessing information freely.
A VPN minimizes these threats by ensuring your activity cannot easily be linked back to you, allowing you to browse and interact online without fear of surveillance.
Enhanced Privacy Tools
Many modern VPN services come equipped with additional features tailored to protect users from specific risks. A kill switch, for instance, is a critical function that immediately disconnects your internet access if the VPN connection drops.
This ensures your online activity is never exposed, even for a moment, maintaining uninterrupted privacy.
Another essential safeguard is DNS leak protection, which prevents your internet traffic from being accidentally routed outside the encrypted VPN tunnel. Without DNS leak protection, your browsing data could inadvertently be exposed to your ISP or other third parties.
Some VPNs also include ad blockers, which improve the browsing experience by stopping intrusive advertisements and reducing the risk of malware infections associated with malicious ads. These tools work in tandem with the VPN’s core security features to create a more private and seamless online environment.
Common Use Cases for VPNs

VPNs are versatile tools that cater to a wide range of needs, making them valuable for personal, professional, and even everyday online use. They go beyond simply enhancing privacy and security by providing solutions for accessing restricted content, ensuring safe communication, and bypassing censorship.
Accessing Geo-Blocked Content
Streaming platforms, news websites, and social media often restrict access to content based on geographic locations. This can be frustrating for users traveling abroad or those living in regions with limited online offerings.
VPNs address this issue by allowing users to connect to servers in different countries, effectively masking their location and bypassing these restrictions.
For example, connecting to a VPN server in another country can grant access to specific video libraries or online services that would otherwise be unavailable. News outlets that limit international readers can also be accessed this way, ensuring you stay informed without barriers.
Additionally, social media platforms blocked in certain regions can be reached just as easily through a VPN connection. This flexibility opens up a world of entertainment and information that might otherwise be out of reach.
Secure Remote Work
The rise of remote work has made secure internet connections an absolute necessity, particularly for those handling sensitive business data. VPNs play a critical role in protecting communication between employees and their companies, especially when connecting to untrusted networks like public Wi-Fi.
By encrypting the connection, VPNs ensure that confidential documents, login credentials, and communications are shielded from prying eyes.
Employers often use VPNs to give remote workers access to internal networks while keeping the organization’s infrastructure secure. Employees can securely share files, access tools, and manage tasks without compromising the integrity of the company’s data.
The added layer of security provided by a VPN minimizes the risks of cyberattacks that could target employees working outside of controlled office environments.
Avoiding Censorship
Internet censorship remains a significant challenge in many parts of the world. Governments, institutions, or organizations block certain websites or platforms to control access to information.
VPNs are a powerful tool for overcoming these limitations, allowing users to bypass firewalls and access restricted sites freely.
By connecting to a server located in a region without such restrictions, users can circumvent censorship policies and browse the web as they normally would. For individuals living in heavily censored areas, VPNs are often the only way to access global news, social media platforms, or communication tools.
This capability is especially crucial for promoting free speech and ensuring that information is not withheld based on location.
Limitations and Considerations

While VPNs offer significant privacy and security benefits, they are not without their drawbacks. It is important to weigh these limitations to ensure you are fully aware of what to expect from a VPN.
Issues such as reduced internet speed, trade-offs between cost and privacy, and legal or ethical concerns can influence how effectively a VPN meets your needs.
Speed Trade-Offs
One of the most common drawbacks of using a VPN is its impact on internet speed. Encryption, which is essential for securing data, can slow down your connection due to the extra processing power required to protect your information.
Additionally, the physical distance between your device and the chosen VPN server plays a significant role in performance. Connecting to servers located far from your actual location can introduce latency, resulting in slower upload and download speeds.
Some VPN providers optimize their servers to balance security and performance, but even the most efficient services may still affect speed to some degree. Users streaming high-definition content or engaging in bandwidth-intensive activities like online gaming may notice these small delays.
Choosing a server closer to your location or selecting a VPN provider known for its speed can help mitigate this issue.
Cost vs. Security
Although free VPN options are widely available, they often come with significant compromises. Many free services generate revenue by logging and selling user data to advertisers, defeating the purpose of using a VPN for privacy.
They may also show intrusive ads, impose strict data limits, or lack advanced features like reliable encryption protocols or kill switches, leaving users exposed to potential security vulnerabilities.
In contrast, paid VPNs typically offer stronger protections, such as no-logs policies, higher-grade encryption, and access to a larger selection of servers. While the cost of a subscription might deter some users, it is often the better choice for those who prioritize privacy and functionality.
Free VPNs can still be useful for casual browsing, but they are not recommended for handling sensitive data or long-term use. Balancing your budget with your security needs is an essential consideration when selecting a VPN.
Legal Restrictions
VPNs are not universally accepted, and laws regulating their use vary significantly across countries. Some regions, such as China and Russia, impose strict bans or restrictions on VPN usage.
Governments in these areas might block access to VPN websites, making it difficult to install or use the service, or criminalize the use of unauthorized VPN providers.
Even in countries where VPNs are legal, using them to bypass restrictions on streaming content, access geo-blocked websites, or circumvent censorship can raise ethical concerns. While VPNs provide the technical ability to bypass such restrictions, it is ultimately up to the user to decide how they navigate legal and ethical boundaries.
Being aware of local regulations and respecting the terms of service for the platforms and websites you access is crucial when using a VPN. Failure to do so could result in penalties or account bans, particularly when accessing content in ways that violate agreements with service providers.
Choosing and Setting Up a VPN

Selecting the right VPN and configuring it correctly are crucial steps in ensuring a secure and reliable experience. With a wide variety of options available, it’s important to understand what to look for in a VPN provider and how to get started.
Features to Prioritize
When evaluating a VPN, certain features should be prioritized to ensure maximum security and performance. A no-logs policy is one of the most critical elements.
Providers that follow this practice guarantee they do not store records of your activity, meaning data like your browsing history or connection timestamps cannot be shared with third parties.
Server availability also plays an important role in creating a fast and flexible connection. A broad server network allows you to connect to different locations worldwide, improving speed and helping you bypass geo-restrictions.
More servers also reduce the likelihood of congestion, ensuring better overall performance.
Encryption strength is another factor to look for. Modern VPNs often use protocols like OpenVPN or WireGuard to provide strong encryption that keeps your data safe from prying eyes.
Additional security features like kill switches, DNS leak protection, and multi-platform compatibility can further improve the service and provide extra peace of mind.
Installation Steps
Setting up a VPN is straightforward and usually requires only a few steps. Start by selecting a VPN provider and creating an account.
Once you’ve signed up, download and install the app for your preferred device, whether it’s a computer, smartphone, or tablet.
After launching the app, log in with the credentials provided during registration. From there, you can explore the server list and select a location.
Choosing a nearby server typically results in faster speeds, while connecting to one in another country can help access geo-blocked content.
Once connected, it’s important to test the connection to ensure it’s secure. Many VPN apps include built-in tools to verify that your IP address is masked and no DNS leaks are exposing your activity.
Running a quick test only takes a moment but offers reassurance that the VPN is working as intended.
Popular Options: NordVPN and ProtonVPN
Two well-known VPN providers, NordVPN and ProtonVPN, offer distinct advantages depending on your needs, providing users with reliable and secure options for enhancing privacy and accessing restricted content. Each caters to different preferences, whether you prioritize advanced features, affordability, or transparency.
NordVPN is widely recognized for its extensive server network, strong encryption protocols, and additional tools like a kill switch and double VPN functionality. It supports fast and reliable connections, making it ideal for streaming, gaming, and bypassing geo-blocks.
For users who need a VPN across multiple devices, NordVPN allows simultaneous connections on up to ten devices with a single subscription. However, it operates on a paid subscription model, which means there’s a cost to access its advanced features and broad server coverage.
ProtonVPN, on the other hand, is known for its strong emphasis on privacy and transparency, with a base offering that includes a free plan. It does not log user activity and provides unlimited data even in its free version, which is rare among VPN services.
While the free plan only includes a limited number of servers and moderate speeds, ProtonVPN’s paid plans unlock additional servers and access to streaming platforms.
It is an excellent choice for those who want a trustworthy, privacy-focused VPN without immediately committing to a paid service.
Conclusion
VPNs have become an essential tool for enhancing online privacy, safeguarding sensitive data, and unlocking access to restricted content. By encrypting your connection and masking your IP address, they provide valuable protection against cyber threats and unwanted surveillance.
Whether securing business communications, bypassing censorship, or enjoying geo-restricted entertainment, a VPN offers versatile benefits that cater to a wide range of needs.
While there are some trade-offs, such as potential speed reductions and the cost of premium services, the advantages often far outweigh the limitations. Selecting a VPN with robust features, setting it up properly, and using it responsibly can significantly improve your online experience.
A well-chosen VPN empowers you to browse, work, and stream with confidence, knowing that your privacy and security are in capable hands.


